THREAT ALERT
Malware – Anatsa Banking Trojan for Android
Tuesday, June 27th, 2023

THREAT ALERT
Tuesday, June 27th, 2023

Since March of 2023 a new mobile malware has been pushing the Android banking trojan “Anatsa” to online banking customers located in the United States, United Kingdom, Austria, Switzerland and Germany. It has since become one of the most prolific banking malware, targeting over 400 financial institutions across the world.
The attackers have been distributing this malware through Android’s Google PlayStore and there have already been over 30,000 installations. The malware is pushed by impersonating PDF Scanners, Adobe Illustrator apps, fitness apps and QR Code Scanners. The attackers took a six-month hiatus before launching a new malvertizing campaign. The malware is still being distributed via apps from Android’s Google PlayStore category office/productivity (PDF Viewer, office suites and editor apps). Below is an app that was previously found on the PlayStore before it was taken down due to being identified as malware:
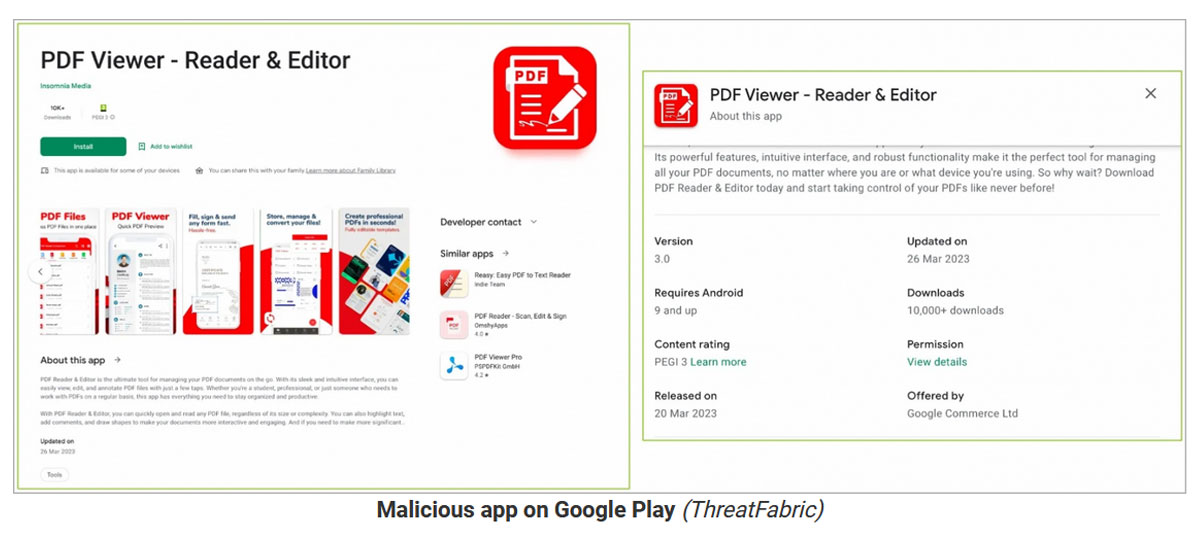
Once the above app was taken down, the attackers continued their campaign by uploading a new dropper under a different impersonation app.
The attackers submitted their impersonator apps in a clean form and then later updated those apps with the malicious code. Once the app was installed on the victim’s device, the dropper apps then request an external resource via GitHub where they then download the Anatsa payloads. These payloads are masqueraded as a text recognizer add-ons for Adobe Illustrator. Once that payload is dropped, Anatsais able to obtain financial information from the victim via overlaying phishing pages when the user attempts to open their legitimate banking app. The payload also collects information via a keylogger.
Anatsa uses the stolen information to conduct on-device fraud. It will perform transactions on the victim’s behalf and begin a money-stealing process for the operators. The stolen money is then turned into cryptocurrency and passed through a rigorous network of money mules until it reaches the attacker.
The trojan features backdoor-like capabilities to steal data and also performs overlay attacks in order to steal credentials as well as log activities by abusing its permissions to Android’s accessibility services API. It can further bypass existing fraud control mechanisms to carry out unauthorized fund transfers.
“Since transactions are initiated from the same device that targeted bank customers regularly use, it has been reported that it is very challenging for banking anti-fraud systems to detect it,” ThreatFabric noted.
It’s important to be vigilant when installing apps on your device from the PlayStore. Be on the lookout for apps that are from dubious publishers, and always check the reviews for any indication of malicious behavior from the app.
Below is the list of the known Anatsa droppers:
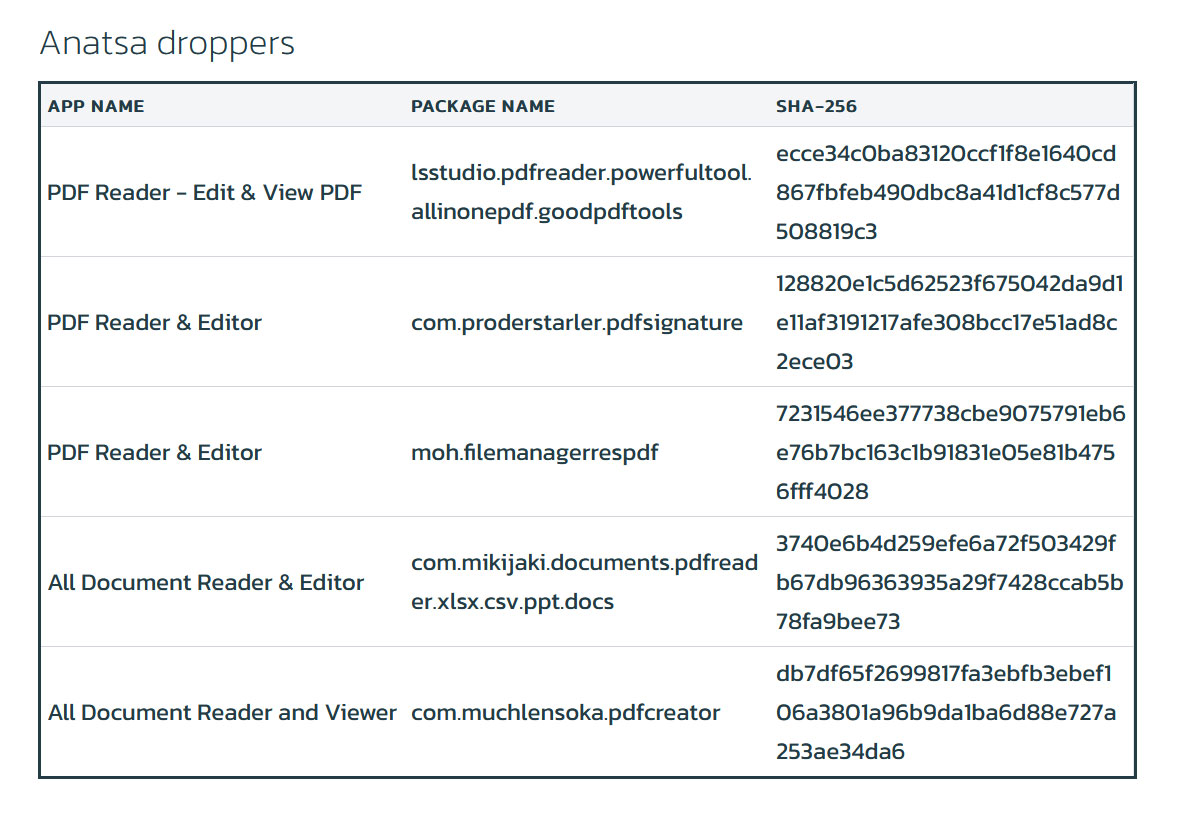
DefenseStorm recommends informing your customer base about the importance of being vigilant when it comes to installing applications from any App store.
Continuous research is being conducted for all newly discovered or recurring malware and ransomware. As always, DefenseStorm recommends the following practices to help secure your environment:
Additional Sources: