DEFENSESTORM
Thought leadership and customer testimonials are some of the many ways we build a community of trust. These cybersecurity resources highlight our recent research and success stories.


Threat Alerts
DefenseStorm is aware of a recent campaign attributed to the Chinese APT group Lotus Blossom targeting Notepad++.

Threat Alerts
Kaspersky researchers have reported that Mustang Panda, a Chinese-linked advanced persistent threat (APT) group, has released an updated variant of its CoolClient backdoor, significantly expanding its espionage functionality.

Threat Alerts
Insider‑driven breaches remain one of the most underestimated security risks facing financial institutions today. Trusted access, whether abused maliciously or through the result of negligence, is something that every organization needs to be aware of. Simply put, understanding, monitoring, and mitigating internal risk has become more critical than ever.

Threat Alerts
This Threat Report highlights four risks that are most likely to impact banks and credit unions in 2026—and that can be addressed with better visibility, stronger governance, and continuous monitoring, not just more point tools.

Datasheets
Over the past 11 months, our co-managed Cyber Operations partnership has delivered measurable impact. Together, we monitored DefenseStorm customers environments at enterprise scale, processing over 5.4 trillion security events (about 16 billion a day) and distilling them down to 379,232 high-fidelity alerts. From there, we drove 47,264 investigations, escalating only 2,862 alerts that truly required your attention.

Threat Alerts
We are following reports indicating that CVE(s) (CVE-2025-59718 CVE-2025-59719) addressed in Fortinet PSIRT advisory FG-IR-25-647 are being actively exploited.

Threat Alerts
This summary outlines the data breach disclosed by Marquis Software Solutions. All details were compiled and summarized from a Bleeping Computer report.
*See update: 12/5

Insights
Nacha has released the 2026 Operating Rules and Regulations, and DefenseStorm breaks down the key points you need to know.

Threat Alerts
Tech support scammers are increasingly targeting banks and credit unions through malicious online ads. These “malvertising” campaigns redirect users to fake Microsoft-branded pages designed to deceive and exploit them.

Case Studies
A Virginia-based Community Bank, employing 145 people and managing over $700 million in assets, faced a cybersecurity incident when a Russian hacker attempted to exploit a system vulnerability introduced by an external consultant. The bank needed robust, real-time monitoring and detection to prevent future attacks and ensure operational resilience.

Case Studies
Reliant Credit Union, with assets amounting to nearly $700M and a membership of 46,615, sought to enhance their risk management program and streamline compliance and internal audits to achieve a more organized and efficient method of tracking progress and meeting regulatory requirements.

Case Studies
Great Lakes Credit Union (GLCU), located in Bannockburn, Illinois, manages $1.4 billion in assets, serves 111,090 members, and employs approximately 231 people. The GLCU fraud team struggled to keep pace with rapidly evolving tactics and faced increasing exposure to sophisticated fraud rings exploiting weaknesses in member-to-member transfers, P2P payments, and ACH channels.

Case Studies
Great Lakes Credit Union (GLCU), located in Bannockburn, Illinois, manages $1.4 billion in assets, serves 111,090 members, and employs approximately 231 people. The credit union faced challenges with disjointed security and risk systems, limited capacity within a small security team, and manual, labor-intensive processes. These issues made it difficult to correlate data for actionable insights and expand cyber event monitoring, leading to inefficiencies in operations and delayed responses to potential threats.

Case Studies
First Financial Bank, headquartered in Abilene, Texas, oversees approximately $14 billion in assets and employs over 1,400 staff across 83 offices. First Financial faced multiple challenges, including inefficient incident monitoring and response, disjointed cybersecurity solutions that led to time-consuming processes, and difficulties in navigating multiple systems to retrieve information during incidents. The bank sought a cyber risk management solution to streamline their ability to manage, monitor, and mitigate cyber events.

Case Studies
A leading Banking as a Service (BaaS) provider, serving over two million accounts and providing disbursement services to more than 750 college and university campuses, struggled with detecting fraudulent accounts. Ineffective processes resulted in undetected financial fraud and high operational costs associated with fund recovery. The organization required a proactive fraud prevention solution to identify and stop fraudulent activity before losses occurred.

Case Studies
With over $8.8 billion in assets, Space Coast Credit Union (SCCU), serves approximately 677,000 members across 67 branches. Prior to their partnership with DefenseStorm, SCCU’s cyber risk management program relied on multiple network monitoring tools, not entirely integrated, which posed challenges in threat detection and reduced the efficiency of their data gathering processes.

Case Studies
Reliant Credit Union, with assets amounting to nearly $700M and a membership of 46,615, serves its community through ten offices and a committed team of 171 employees. As cybersecurity threats became more sophisticated, the credit union faced challenges in managing and mitigating risks effectively. Reliant recognized this urgent need and embarked on a transformative journey to enhance its ability to monitor, manage, and report on cyber events.

Case Studies
Red Rocks Credit Union, with approximately $340 million in assets, 48 employees, and nearly 40,000 members, struggled with manual, time-consuming cybersecurity processes and limited visibility into its security posture. The institution needed improved reporting, direct alert notifications, and adherence to regulatory frameworks such as GLBA and NIST.

Case Studies
Lone Star Credit Union, based in Dallas, Texas, manages $180 million in assets, serves more than 11,000 members, and employs 41 staff. The credit union faced operational inefficiencies due to outdated systems, network issues, and slow servers, all of which hindered productivity and member service quality.

Case Studies
Live Oak Bank, headquartered in Wilmington, North Carolina, employs around 1,015 people and manages assets exceeding $13 billion. As the bank expanded into transaction accounts, it required a real-time monitoring system capable of analyzing transaction and digital activity efficiently to prevent fraud and ensure compliance.

Case Studies
Prevail Bank, located in Medford, Wisconsin, operates with $970 million in assets and 121 employees. The bank’s existing Security Information and Event Management (SIEM) solution offered limited log coverage and visibility, hindering its ability to monitor systems effectively and respond quickly to potential threats.

Case Studies
NuMark Credit Union, based in Joliet, Illinois, manages approximately $875 million in assets, 172 employees, and serves 62,000 members. With only one in-house system administrator, the institution struggled to manage increasing cyber risk levels using existing tools that lacked sufficient monitoring and response capabilities.

Case Studies
nCIno, a global financial technology company providing a cloud-based bank operating system to more than 1,750 financial institutions, needed an advanced cyber risk management platform to enhance monitoring, anomaly detection, and reporting. The company sought a more efficient solution to improve visibility and response times across its network infrastructure.

Case Studies
Our Community Credit Union, headquartered in Shelton, Washington, manages over $600 million in assets with 107 employees serving about 32,000 members. The credit union needed a comprehensive cyber risk management solution that could provide 24/7 monitoring, compliance support, and quick implementation to align with its growing strategic initiatives.

Case Studies
Members Credit Union, with over $400 million in assets, 117 employees, and 48,000 members, was operating without enough visibility into their systems and did not have the bandwidth to efficiently keep up with the everyday process of cybersecurity monitoring and management. It was simply impossible to manually monitor and keep up with the volume of logs and events their systems were generating. With a goal to find a vendor to support their smaller internal cyber team, Members CU sought a partnership in cyber risk management that could not only assist in monitoring but also provide 24/7/365 support.

Case Studies
First Financial Bank, headquartered in Abilene, Texas, oversees approximately $14 billion in assets and employs over 1,400 staff across 83 offices. First Financial faced multiple challenges, including inefficient incident monitoring and response, disjointed cybersecurity solutions that led to time-consuming processes, and difficulties in navigating multiple systems to retrieve information during incidents. The bank sought a cyber risk management solution to streamline their ability to manage, monitor, and mitigate cyber events.

Case Studies
First Bank Elk River, located in Minnesota, manages over $360 million in assets with 46 employees serving nearly 5,000 customers. The institution’s previous cybersecurity provider failed to deliver reliable and streamlined reporting capabilities, hindering its ability to meet regulatory and security monitoring needs efficiently.

Fraud Squad
When 89-year-old Victoria (Canada) resident picked up the phone, the caller ID displayed: Canadian Imperial Bank of Commerce (CIBC) Fraud Department. What followed was a months-long deception that ended with nearly $1.7 million in cash, bank drafts, and gold gone.
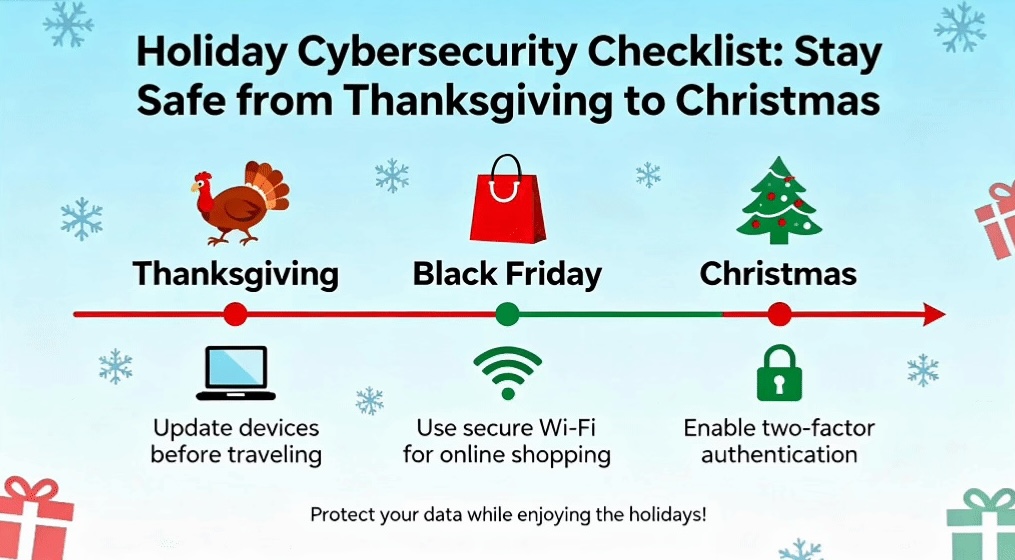
Insights
As you prepare for the holidays, it’s important to remember that cybercriminals are preparing too! Now is the perfect time to strengthen your cybersecurity! Here are some important tips to keep your data and devices safe while you enjoy the holidays!

Case Studies
Canvas Credit Union, based in Lone Tree, Colorado, serves over 300,000 members and holds more than $4 billion in assets. The institution faced the challenge of demonstrating continuous and comprehensive cybersecurity oversight. It needed a system capable of aggregating and analyzing log and firewall data around the clock to ensure account safety and compliance confidence.